Human-Centered Security
| Semester: | 2019 Summer |
| For: | Master |
| Format: | Lecture |
| Credit Points: | 5 CP |

Master-level lecture covering concepts and advances of human centered IT security. Topics include the design, planning, execution, and statistical analysis of studies, basic research methodology, and recent advances in human-centered security.
Important Dates
- 2019-04-09 14:00 - 17:00 | First Lecture (Room F107)
- 2019-09-13 14:00 - 16:30 | Exam (Room VII 201, Königsworther Platz 1, Lecture Hall)
- 2019-10-14 16:00 - 17:00 | Exam Review (Room A445, Welfengarten 1)
Structure
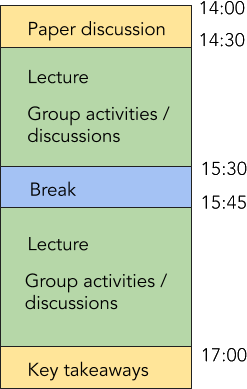
Weekly combined lecture & exercise on Tuesdays starting at 14:00 in Room F107, Welfengarten 1.
Covered Topics
- Overview of the human-centered security and privacy field
- Introduction to HCI methods and the design of experiment
- Specific usable security and privacy topics
Lectures
| 0 | 2019-04-09 | Introduction |
| 1 | 2019-04-16 | Usable Crypto |
| 2 | 2019-04-23 | Privacy, Ethics & Bias |
| 3 | 2019-04-30 | Passwords & Experimental Design |
| 4 | 2019-05-07 | Experimental Design & Phishing |
| 5 | 2019-05-14 | Surveys |
| 6 | 2019-05-21 | Security Warnings |
| 7 | 2019-05-28 | IoT & Data Processing |
| 8 | 2019-06-04 | Permissions & Hypotheses |
| 9 | 2019-06-18 | Permissions & Hypotheses (II) |
| 10 | 2019-06-25 | Anonymity & Correlations |
| 11 | 2019-07-02 | Censorship & Data Visualization |
| 12 | 2019-07-09 | Security for Activists & Journalists |
Exam
The exam date and rooms will be announced.
A second chance to take the exam will be offered next semester (winter). Bonus points from this semester are eligible for the next semester exam.
During the exam, you are allowed a double-sided, handwritten A4 paper and a non-programmable calculator. Additional scratch paper will be available.
Bonus Points
Bonus points for the lecture (equivalent to one grade step for the exam) are awarded for reading and summarizing a minimum of 8 out of 12 weekly announced research papers.
Further Reading
No textbook is required for this course, but the selection below can give you further insights into human-computer interaction and usable security and privacy research:- “Research Methods in Human-Computer Interaction” by Jonathan Lazar, Jinjuan Heidi Feng, and Harry Hochheiser
- “Engineering Security” (PDF) by Peter Gutmann
- “Usable Security: History, Themes, and Challenges” by Simson Garfinkel
- “Security and Usability: Designing Secure Systems That People Can Use” by Lorrie Faith Cranor and Simson Garfinkel
