Poster: A Large Scale Investigation of Obfuscation Use in Google Play
In 26th Annual Network and Distributed System Security Symposium, NDSS 2019, San Diego, California, USA, February 24-27, 2019
Poster
Abstract
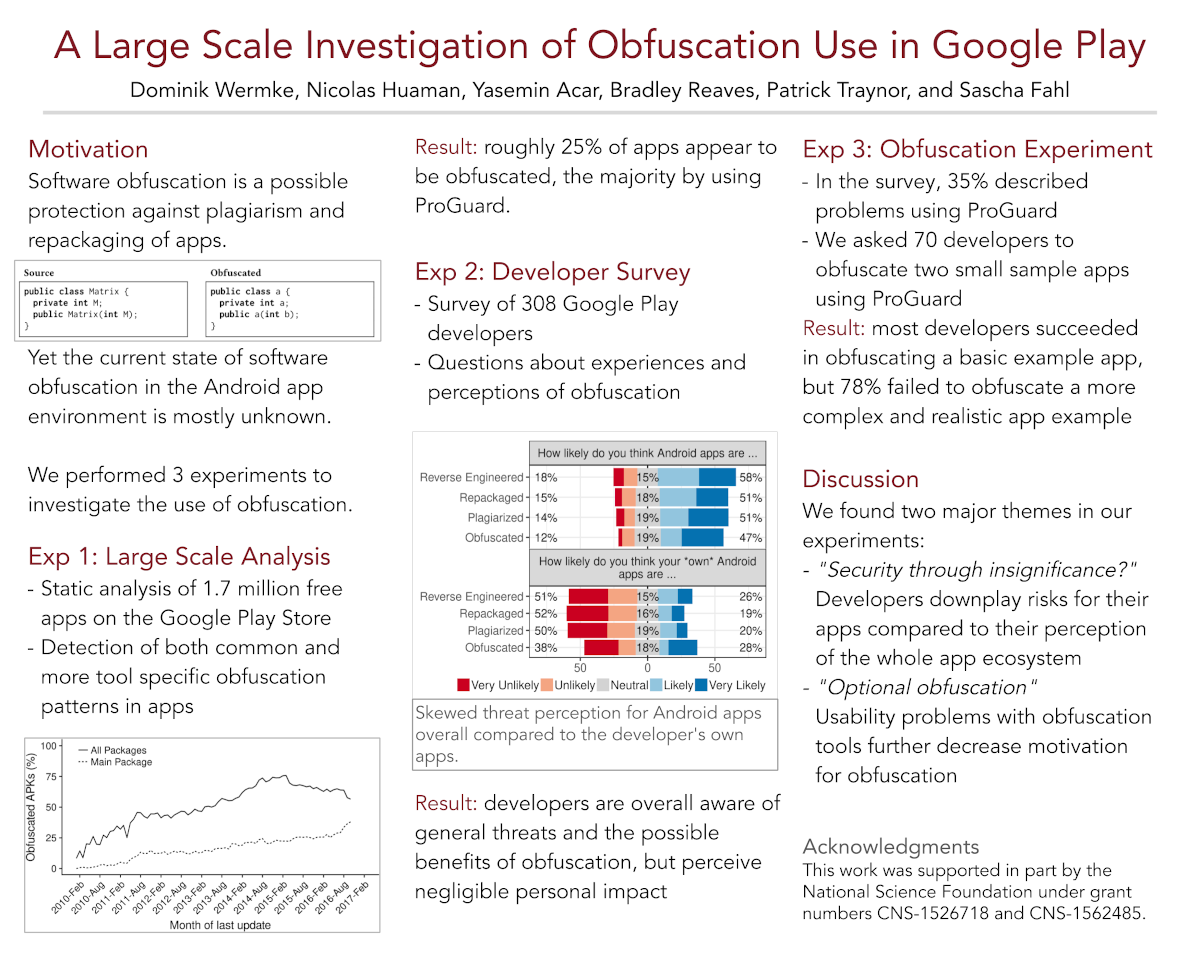
Android applications are frequently plagiarized or repackaged, and software obfuscation is a recommended protection against these practices. However, there is very little data on the overall rates of app obfuscation, the techniques used, or factors that lead to devel- opers to choose to obfuscate their apps.
In this paper, we present the first comprehensive analysis of the use of and challenges to soft- ware obfuscation in Android applications. We analyzed 1.7 million free Android apps from Google Play to detect various obfuscation techniques, finding that only 24.92% of apps are obfuscated by the developer. To better understand this rate of obfuscation, we surveyed 308 Google Play developers about their experiences and attitudes about obfuscation. We found that while developers feel that apps in general are at risk of plagiarism, they do not fear theft of their own apps. Developers also report difficulties obfuscating their own apps. To better understand, we conducted a follow-up study where the vast majority of 70 participants failed to obfuscate a realistic sample app even while many mistakenly believed they had been successful.
These findings have broad implications both for improving the security of Android apps and for all tools that aim to help developers write more secure software.
Reference
@misc{poster/ndss/wermke19b,
author = {Dominik Wermke and
Nicolas Huaman and
Yasemin Acar and
Bradley Reaves and
Patrick Traynor and
Sascha Fahl},
howpublished = {In 26th Annual Network and Distributed System Security Symposium, NDSS 2019, San Diego, California, USA, February 24-27, 2019},
month = {Feb},
title = {A Large Scale Investigation of Obfuscation Use in Google Play},
url = {https://www.ndss-symposium.org/wp-content/uploads/2019/02/ndss2019posters_paper_40.pdf},
year = {2019}
}