Poster: Unsafe Rust - Conscious Choice or Spiky Shortcut?
In 43rd IEEE Symposium on Security and Privacy, IEEE S&P 2022, May 23-26, 2022
Poster
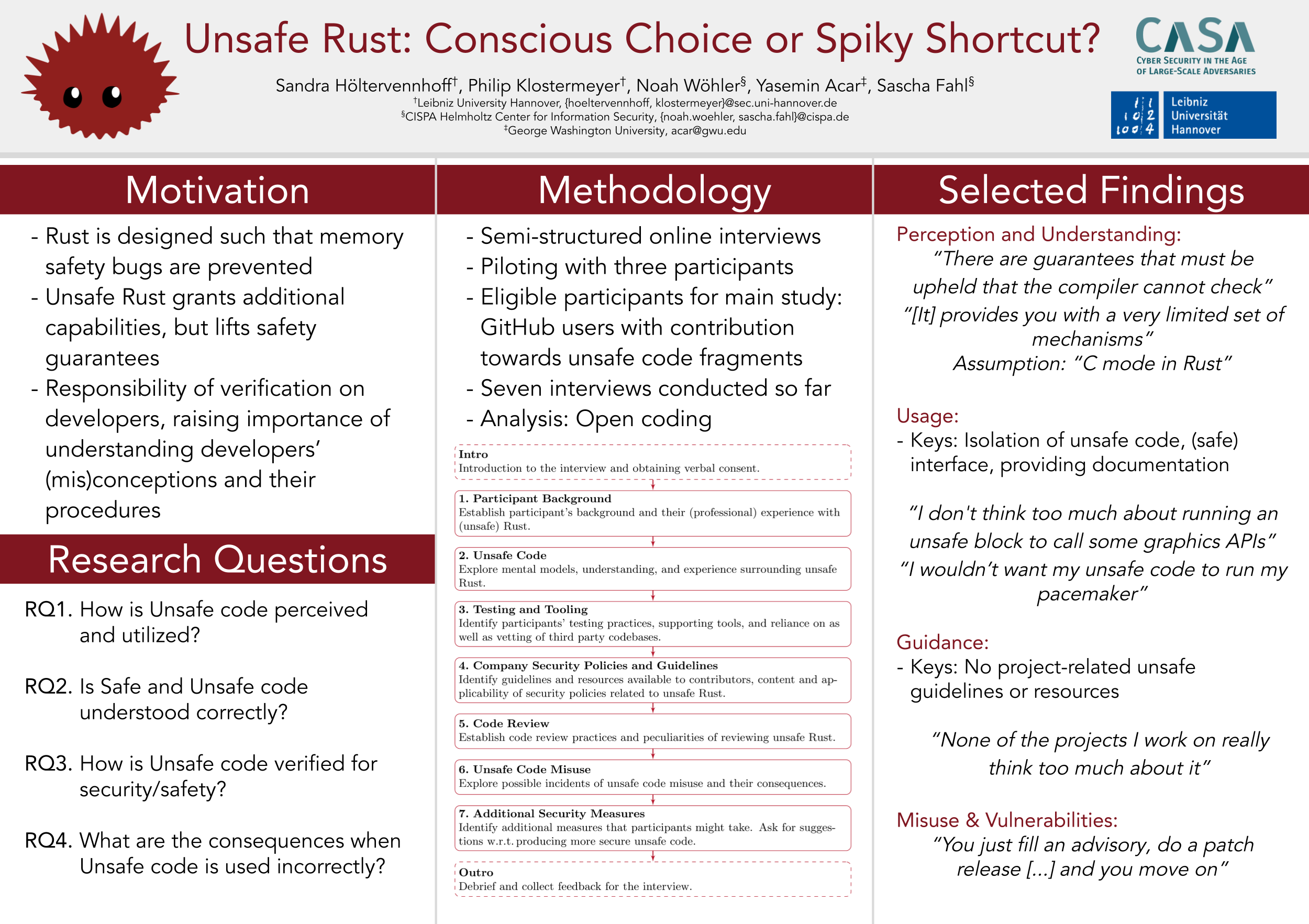
Abstract
The Rust programming language features guarantees regarding memory safety, which get enforced during compile time. So called unsafe Rust partly lifts guarantees to enable a programmer to write code which cannot be verified by a compiler to be memory safe, thus, creating critical points during development susceptible to serious security bugs. In this project, we investigate the usage of unsafe Rust by conducting qualitative, semi-structured interviews with Rust developers on (1) how the process of coding unsafe Rust looks like, (2) whether they reconsider the usage of this critical (and potentially dangerous) part of the language, and (3) how they verify the code’s correctness and soundness.
The interviews coded so far show that the awareness of the potential for security bugs, when using unsafe Rust, can be considered high among participants, but also that there are still misunderstandings about what unsafe Rust does technically. As for help in writing secure unsafe Rust, no procedures were found besides official documentation. Mostly, the lively exchange in Rust communities and personal experiences help developers to evaluate their unsafe code fragments.
Reference
@misc{poster/oakland/hoeltervennhoff22,
author = {Sandra Höltervennhoff and
Philip Klostermeyer and
Noah Wöhler and
Yasemin Acar and
Sascha Fahl},
howpublished = {In 43rd IEEE Symposium on Security and Privacy, IEEE S&P 2022, May 23-26, 2022},
month = {May},
title = {Poster: Unsafe Rust - Conscious Choice or Spiky Shortcut?},
url = {https://www.ieee-security.org/TC/SP2022/program-posters.html},
year = {2022}
}